Convequity's Cybersecurity Research
We discuss the hot markets we'll be publishing research on during the next few months
Summary
This is a post to share the cybersecurity research we’ll be publishing at convequity.com over the next few months.
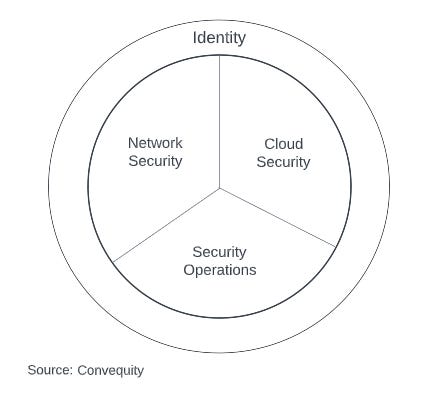
Firstly, we would like to simplify cybersecurity by dividing the industry into;
network security,
cloud security,
security operations, and
identity management.
In the following content, we’ll briefly outline the mature and high-growth areas of each category, and let subscribers know what we intend on researching during the next few months.
Note: for those institutional investors interested in expert calls or acquiring tailored research on any of the following categories and subcategories, please book a 30 minute call with us to discuss.
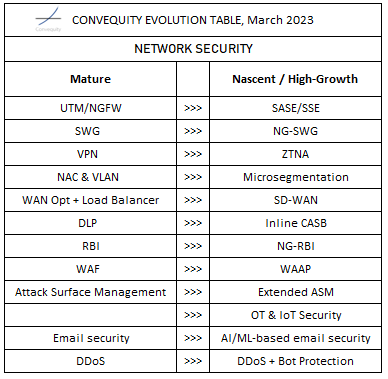
Network Security
Expedited by the pandemic and the ensuing urgency for digital transformations, network security has fragmented into a few different directions. SASE and then SSE has received increasing demand as a way to securely connect remote employees with disparate IT resources. SD-WAN has emerged to improve network performance and reduce costs associated with connecting globally distributed enterprises. OT and IoT security have gained attention for helping the unmodernised verticals securely modernise. Email security, albeit a largely commoditized area, is experiencing a step-up in innovation and growth as players attempt to counter the growing sophistication of email-based attacks with AI/ML capabilities. We also think NG-RBI (Next-Gen Remote Browser Isolation), microsegmentation, and extended ASM, are spaces where innovative startups are building strong reputations.
In approximately the next four months, we intend on revisiting or extending our research in;
SASE – a market that has consolidated down to a few major public and private names. Palo Alto Networks, Cloudflare, Zscaler, Fortinet, and Netskope are the major players that we’re going to evaluate. Cato Networks and Perimeter 81 are two smaller players that are also worth reviewing.
OT & IoT security – a very nascent and high-growth segment of network security, with substantially less hype. In a similar vein to how we’ve recently published a cloud security series focusing on Palo Alto Networks and the surrounding startup competition, we will do the same for Fortinet and the surrounding OT & IoT security startup competition.
Email security – this is a very interesting market right now. The traditional SEGs (Secure Email Gateway) are architecturally dated, requiring much time and effort to deploy. However, once they are operational, they are really effective with broad functionality. Alternatively, the ICES (Integrated Cloud Email Security) vendors leverage rich API connectivity to gain visibility and management capabilities within cloud email service providers, in order to do email security, thus making them super easy to deploy by comparison. These cleaner slate startups in this space are also pioneering ML-based detections to combat sophisticated targeted attacks and BEC (Business Email Compromise). However, right now it’s not clear whether these ICES vendors have enough competitive edge to uproot the incumbent SEG vendors. This is what we want to investigate, and our interest has been piqued because of Cloudflare’s acquisition of Area 1 Security last year. The scale and density of Cloudflare’s global network is going to feed colossal volumes of data into Area 1’s leading ML-based email security platform. This could potentially be a game changer for the email security industry once Cloudflare fine tunes the GTM strategy. This is what we shall evaluate.
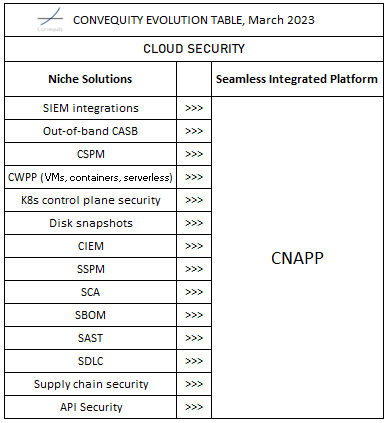
Cloud Security
Cloud security is the most fragmented category of cybersecurity, and as we shared in our Cybersecurity Review 2023 report, we think the market is now at peak fragmentation. By considering the demand side and funding side dynamics, going forward it looks as though we will see a notable degree of net consolidation. If this transpires, then CNAPP (Cloud-Native Application Protection Platform) vendors will prevail over more narrowly defined startups. Hence, rather than focus on niche solutions, investors and stakeholders in general, ought to consider which vendors will most likely succeed in the race toward the truest CNAPP.
During approximately the next four months, for cloud security we intend on researching;
Sysdig – to add to the Cloud Security Series, and compare them to Palo Alto’s Prisma Cloud and the private names we’ve covered thus far.
SentinelOne & CrowdStrike – additionally, we may extend the research into SentinelOne’s and CrowdStrike’s cloud security offerings (although we did cover a comparative discussion of the two rivals CWPP in our recent SentinelOne vs CrowdStrike report) and add this to the Cloud Security Series.
API Security – this is a space of huge innovation, whereby pure-play API security startups are increasingly competing with larger names from the WAAP (Web Application & API Protection) space. API security is also an intriguing space because it is not only part of cloud security, it transcends to network security as well.
SIEM Integrations (or more broadly, security data solutions) – we believe that Palo Alto and SentinelOne, which have made big investments to own the data layer, have the long-term advantage in the XDR market. This ought to also provide competitive advantages in the cloud security market. However, the likes of Wiz and Orca have very good SIEM integrations whereby they interoperate their next-gen SOAR to abstract away many pain points associated with SIEMs. Therefore, we want to dig a bit deeper and compare Prisma Cloud & XSIAM against Wiz/Orca & SIEM.
Serverless security – this is a very innovative space. Serverless compute has been around for many years but adoption has been slow. DevOps teams are gradually becoming more comfortable, however, which opens the door for serverless security innovation. Conducting runtime protection in serverless compute requires the deployment of binary files into the function. These binary files are extremely lightweight agents, and while they are limited in scope, the technology behind them could help pioneer lighter weight form factors of agents at lower level of abstractions (i.e., containers, VMs, etc.). Therefore, getting a better understanding of serverless will likely help us better evaluate the future role of agents within cloud security.
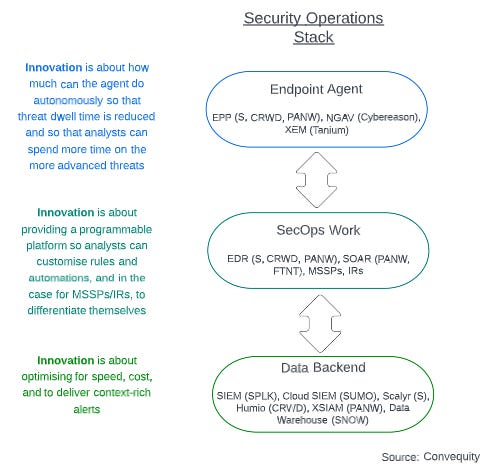
Security Operations
To simplify the complexity of security operations, it is useful to break it down into 1) the data management backend, 2) the work that SecOps analysts do, and 3) the endpoint agent.
We consider this a huge TAM within cybersecurity. Firstly, the majority of enterprises still have mass signature-based AV deployments, such as Symantec and McAfee. This means there is still a long runway of growth for vendors related to EPP, NGAV and EDR, and even for endpoint security leader CRWD which has reached $2bn in TTM revenue. Secondly, as mentioned earlier, there is a huge innovation space related to automating workflows for SecOps analysts. And thirdly, for those vendors willing to spend big on revamping the data backend, there is significant value they can deliver to enterprises and MSSPs.
Over approximately the next four months, we intend on researching the following in relation to security operations:
SentinelOne & CrowdStrike vs XDR Startup/Private competition – in a similar vein to the research on Palo Alto Networks vs cloud security startups and what we intend on doing on Fortinet vs OT security startups, we will also further investigate SentinelOne and CrowdStrike and their XDR startup competition.
Identity
Within identity our main focus is Okta. We’ve done a lot of research into Okta but we need to revisit the thesis and evaluate the Microsoft threat, legacy competition, and the startup space surrounding Okta.
Over approximately the next four months, we intend on publishing the following identity related research:
Okta vs Microsoft Entra – Microsoft has ramped up their identity access management suite, rebranding it as Entra, and further integrating it into the Microsoft ecosystem. We need to assess the incremental competitive threat this poses to Okta and evaluate Okta's roadmap to becoming the first true CARTA (Continuous Adaptive Risk & Trust Assessment) provider.
Okta vs Thoma Bravo (SailPoint, Ping Identity, ForgeRock) & CyberArk – Okta’s IAM space has become largely commoditized and hence the company is venturing into IGA and PAM. The IGA and PAM competition is mainly with legacy names that are entrenched and difficult to disrupt. We plan on evaluating how long it may take Okta to disrupt with its cloud-native approach.
CIAM – we will revisit the CIAM market and Okta’s progress in integrating Auth0, as well as revisiting Auth0’s strengths versus other CIAM players.
Passwordless - possibly we'll take a look at developments in the passwordless market as this looks to be destined to be a big part of access management in the not-too-distant future.