Fortinet - A Vision Beyond SASE
We provide reference framework for thinking about Fortinet's future in converged networking and security
Summary
FTNT's unique approach to the Secure Access Service Edge (SASE) distinguishes it as a highly adaptive vendor poised for the evolving landscape of networking and network security. We have developed a variant named Secure Access Service Omni (SASO) to more accurately reflect FTNT's prowess in blending networking and security capabilities. We envision SASO will gradually overshadow SASE in the long term. Nevertheless, the journey through SASE or SASO represents just the initial phase in the expansive domain of networking and security. This summary also delves into FTNT's potential growth in the intermediate and final stages of networking/security. From a valuation standpoint, FTNT presents an appealing investment opportunity, with our analysis indicating a potential for approximately 50% upside ($100 PT), especially when looking beyond near-term market guidance.
Let’s Recap the Journey to Date of SASE and FTNT
Ever since Gartner introduced the concept of SASE back in 2019, it has pretty much taken over the conversation in both networking and network security circles. Right after Gartner threw SASE into the limelight, there was a rush of vendors from both the networking and network security sectors, each one clamoring to claim they were the true SASE pioneers. Yet, that claim was a stretch for most. Networking giants with SD-WAN technologies like CSCO, alongside cloud-based network security firms like ZS, were missing pieces of the puzzle. This mismatch led to a bunch of companies falling for the hype, choosing providers they thought offered a complete SASE solution, only to find out they would need a slew of third-party integrations to get it running properly — skyrocketing their TCO.
The initial letdown with SASE can be largely pinned on how Gartner chose to promote it, opening doors for vendors to exaggerate claims and muddying the waters for everyone. Gartner's original SASE reveal was broad and vague, lacking in details or direct vendor comparisons. Meanwhile, Gartner kept updating their Magic Quadrant (MQ) for WAN Edge Infrastructure (later dubbed SD-WAN in 2022), which covers the networking aspect of SASE. Yet, it took them almost three years to release an MQ for the security dimension of SASE, in February 2022, which they named SSE (Secure Service Edge).
Wouldn't it have been easier to just release an MQ for SASE as a whole? Sure, but it seems Gartner was dealing with its own internal drama, perhaps political, that kept the networking and network security teams from syncing up for a unified approach.
From the get-go in 2019, we've been banging the drum that FTNT was going to eventually emerge as a top player in SASE. This stance was, and still is, somewhat against the grain, especially since Gartner took a long while even acknowledging FTNT in its SASE discussions. Gartner's take on SASE is strictly cloud-based - meaning, they believe that robust networking and security should not just converge but also be executed off-premises, in the nearest PoP. We've always agreed with the "convergence" part because it's clear that ditching complex service chains boosts both user experience and security. However, Gartner's insistence on cloud/edge PoP execution never made sense to us.
In our view, the convergence of networking and security — SASE, that is — should happen wherever it makes the most economical sense, depending on an organization's IT setup. Let's break it down:
For enterprises deeply embedded in the cloud, using mostly SaaS apps, with fewer offices and many remote workers, aligning with Gartner's SASE vision and executing in the PoP is economically sound.
However, for businesses with a hybrid IT landscape — juggling cloud-based SaaS and on-premises applications, numerous branches or retail locations, and a largely office-bound workforce — Gartner's SASE model doesn't quite fit.
For the latter scenario, deciding between PoP-based or on-premises SASE boils down to where the applications are hosted, the ratio of remote workers, and the proximity of a branch to a PoP. If internal (east-west) traffic is prevalent, it's more efficient to handle the converged networking/security at the branch level before routing it via the WAN, sidestepping PoP screening. This suggests a blended approach — partially on-premises, partially in PoP — could serve especially well for the second type of enterprise.
Fortinet stands out, for better and for worse, as the lone vendor capable of delivering pure converged networking and security onsite without any service chaining. It's arguable whether they're also the only provider that can do the same in a PoP setting. The upside is Fortinet's unique position in the SASE marketplace, boosting its competitive edge. The downside? This uniqueness has somewhat backfired, as Gartner, for quite some time, sidelined them in SASE evaluations, impacting their market strategy execution.
Fortinet truly stands out in the field, thanks to their dedication to developing custom silicon. These ASIC chips are engineered specifically for the heavy lifting required in networking and security operations. The blend of these ASICs with their proprietary hardware and the robust FortiOS operating system means Fortinet can pack a complete range of networking (like routing and SD-WAN) and security (such as NGFW, SWG, ZTNA, etc.) features into a single, economical, and compact FortiGate appliance. This approach not only boosts performance but also slashes both computational and managerial expenses, a stark contrast to the traditional, more costly method of linking separate appliances for each function. For similar levels of performance per dollar, competitors often resort to processing traffic through their PoPs. Moreover, the compact nature of the FortiGate makes it versatile for various settings, from large to small branches, even fitting neatly into home office setups.
To give credit where it's due, in SASE's early stages, Fortinet's on-prem converged networking/security solutions hadn't fully transitioned into a cloud-native, multi-tenant model. However, labeling this as a shortfall seemed a bit unfair, especially considering that other vendors Gartner spotlighted had their own limitations within SSE, an area where Fortinet didn't falter. Despite these early critiques, Fortinet swiftly migrated their on-prem expertise to cloud-based SASE solutions. Now, with Fortinet, companies have the flexibility to host their 'PoP' on-site or off-site, managing their SASE infrastructure from anywhere, all thanks to Fortinet's well architected FortiOS. This adaptability and performance, driven by their silicon and software synergy, have positioned Fortinet as the most accommodating and efficient SASE provider since 2020.
Our longstanding belief in Fortinet's SASE prowess was somewhat acknowledged by Gartner in late 2022 with the release of the Single Vendor Guide to SASE. Although not a Magic Quadrant, this guide was a significant step towards clarifying the market, particularly in addressing the confusion caused by conflicting narratives in the SD-WAN and SSE spaces. This move by Gartner, however, felt more like a reaction to the market's consolidation trend, where frustration over separate evaluations for SD-WAN and SSE spurred a wave of mergers and acquisitions. Beginning in the first half of 2022, we saw major moves like AVGO acquiring VMware, Netskope snapping up Infiot, HPE grabbing Axis Security, and Versa developing its SSE suite — all aiming to create a unified SASE offering. This market shift, with vendors merging SSE and SD-WAN capabilities, mirrored what Fortinet had been doing all along: seamlessly integrating SD-WAN and SSE into a single SASE solution.
While the market has seen a few players now positioned as single-vendor SASE providers, Fortinet's in-house development of their platform — barring a minor acquisition for cloud-delivered ZTNA — sets them apart. This approach minimizes technical debt compared to competitors, empowering Fortinet to continue innovating swiftly, a trend they've maintained over recent years.
From SASE to SASO
Amidst the COVID-19 pandemic, many were quick to crown Gartner's SASE model as the ultimate solution for networking and security. Yet, as we navigated through continued cloud adoption, it became evident that hybrid IT setups were not diminishing. Despite the push towards cloud services, a mix of factors — costs, regulatory demands, existing technical frameworks, and security worries — meant that a significant on-prem footprint remained indispensable for many organizations. This reality cast doubt on the notion that cloud-based networking and security could entirely supplant traditional data centre models.
The belief that SASE represented the zenith of evolution in this space was always a bit of a stretch. History shows us that the tech world oscillates between centralized and decentralized models in a quest for better performance and simplicity. From the centralized era of telecommunications in the late 19th and 20th centuries to the decentralized dawn of the internet in the late 20th century, and swinging back to the centralized nature of Web 2.0, this cycle has repeated across various domains, cybersecurity included. SASE's centralized framework has gained traction, but we're witnessing a push towards decentralization, with some vendors starting to offload specific SSE processing onto user devices, aiming to enhance performance and reduce costs.
These observations, coupled with our respect for FTNT's integrated approach to networking and security, led us to propose an evolution from SASE to SASO (Secure Access Service Omni) in 2023. The substitution of 'Edge' with 'Omni' in the acronym mirrors our belief that converged networking and security should be implemented wherever it makes most sense economically and in terms of performance — be it on-premises, in edge PoPs, or at home offices. We anticipate this broader perspective will increasingly take precedence, reflecting the ongoing reality of hybrid IT landscapes and the pendulum swing between centralization and decentralization.
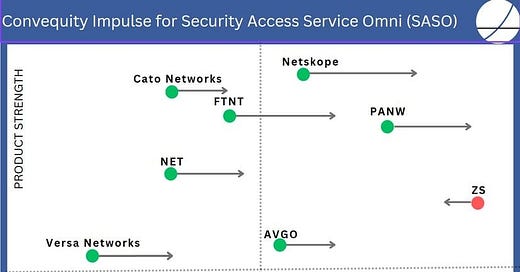
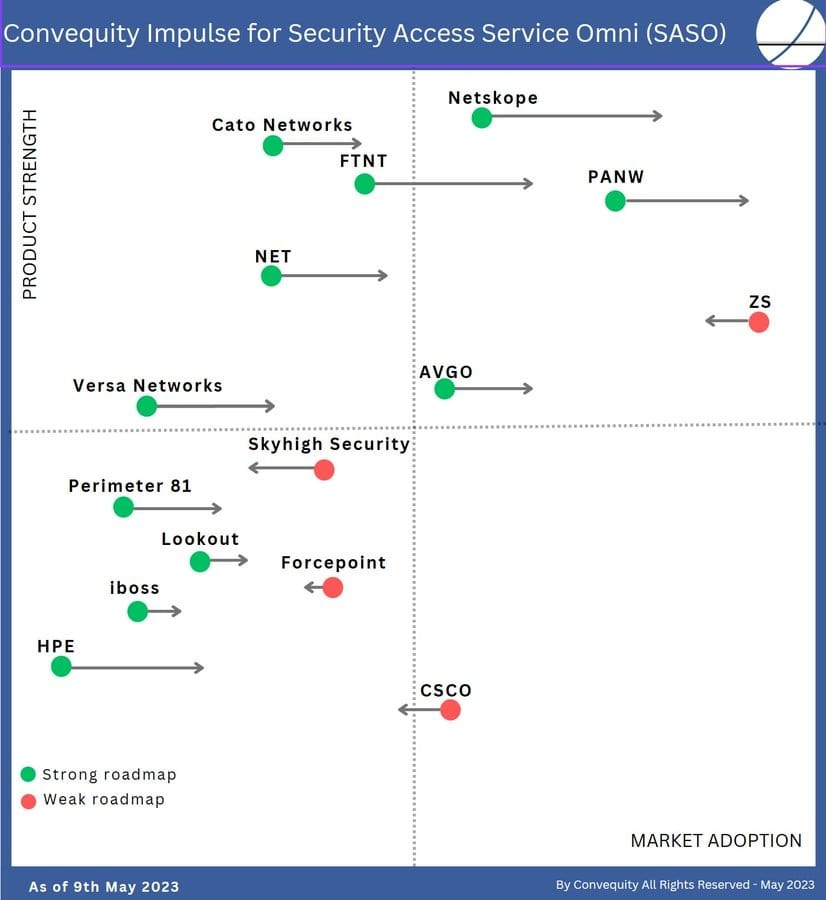
To evaluate vendors through the SASO lens, we introduced the Convequity Impulse last year. This model assesses vendors on two fronts: Market Adoption (x-axis) and Product Strength (y-axis), as of May 2023. The future market trajectory, projected over the next two years, is represented by horizontal arrows: rightward for anticipated market share growth and leftward for a decline. The present Product Strength primarily informs these predictions, alongside the vendor's product roadmap — a crucial element in forecasting, especially for those currently ranked lower in Product Strength yet poised for growth due to strategic future plans.
We delve into each vendor's positioning within the Convequity Impulse in our comprehensive Investor Guide to SASE and the SD-WAN & SASE Industry Review, exclusively for Convequity subscribers. Additionally, we're gearing up to revisit the Convequity Impulse for 2024 soon.
Beyond SASE & SASO – Mapping the Future of Secure Networking
Right now, SASE attracts most of the attention in the realm of networking and security evolution. But, to be honest, it's just a slice of the larger pie. Echoing insights from Dell’Oro, the entire network/security spectrum is better understood through the lens of the first, middle, and last mile — terms that describe the data packet's journey.
The first mile, or the WAN Edge, is the domain of SASE. It's basically how far data travels from a user and their device to where networking and security is processed. Under the traditional SASE model, this means the leap to the PoP. But with our shift to SASO, it's either to the PoP or an on-prem gateway handling SD-WAN and SSE, if an enterprise is using Fortinet, for example.
Yet, the first mile is just the beginning. Data packets have more ground to cover to reach their cloud or data centre destinations. After getting processed in a PoP (using SASO parlance, that could be an edge or on-prem PoP), they venture through the middle mile — navigating a web of interconnected networks. Finally, in the last mile, packets arrive at their destination, be it a cloud-based SaaS application or an internal data center app.
While there is vendor consolidation happening in the first mile, the middle and last miles are still a jumble of different providers. Over time, there's likely a push for more unified solutions across all three stages. Otherwise, the efficiency of a low latency first mile gets lost amid the hiccups of the subsequent miles, undermining the quest for a better user experience.
FTNT seems poised to capitalize on the anticipated consolidation across all miles, though this investment thesis will play itself out over a long timeframe, spanning the decade, given the sluggish pace of networking evolution. Let's break down FTNT's positioning across these stages.
The First Mile
Here, it's all about SASE or SASO, where FTNT shines due to its versatile FortiGate for on-prem processing and FortiSASE for edge operations. FTNT's true convergence outpaces competitors who rely on service chaining due to missing native capabilities or piecemeal solutions. Despite trailing giants like ZS and PANW in SASE market share, FTNT's vast customer base, bolstered by its FortiGate deployment, sets a solid foundation for growth, especially as it pivots to monetize its SASE offerings more aggressively.
The Middle Mile
Currently, FTNT is not leading in the middle mile segment, lagging behind top SASE players like NET, AKAM, and Netskope, known for their intricately developed and globally expansive peering networks. NET and AKAM, with their vast CDN networks, naturally dominate the middle mile. Yet, other significant players, such as EQIX, who offers colocation data center services and network connections between PoPs, and Graphiant with its NaaS offerings, are also key in this space due to their dense and widespread PoP networks. FTNT has set ambitious goals to own more than 100 PoPs, a stark contrast to competitors who typically lease colocation facilities, such as those from EQIX. This unique approach by FTNT, despite its high initial costs, is expected to offer long-term flexibility and allow for the optimal design of their ASIC architecture.
In the interim, FTNT has utilized Google's Cloud network to swiftly increase its PoP footprint, mirroring PANW's SASE strategy. This move is seen as a stopgap, aiming to bridge the gap in SASE coverage but is anticipated to be a temporary solution. The reliance on Google's infrastructure, while expanding FTNT's PoP reach, does mean increased COGS and pressure on gross margins due to the absence of their proprietary ASICs in these PoPs. However, FTNT is also expanding its PoP network through collaborations with EQIX for a more gradual expansion that accommodates their ASIC technology.
FTNT's strategy encompasses a fourfold approach: building proprietary PoPs, leveraging Google's infrastructure, utilizing EQIX's colocation services, and developing PoPs in partnership with service providers (SPs). This latter strategy is particularly strategic, as it targets a market segment underserved by the pricing models of competitors like ZS and PANW. By providing the hardware and software for SASE without the management overhead, FTNT enables SPs to offer competitive SASE services at a lower cost, appealing to price-sensitive service providers.
This comprehensive strategy positions FTNT as an emerging contender in the NaaS market, catering to organizations looking to shift from capital-intensive networking to an operational expense model. In the short term, FTNT has solidified its presence in the middle mile, complementing its enhanced first mile coverage. Over time, the goal is to achieve a network predominantly powered by FTNT's own technology and architecture, potentially increasing its terminal FCF margin significantly from its current level.
The challenge for FTNT in achieving this vision lies in the need for exceptional talent capable of designing a best-of-breed, next-generation global network — a task that demands expertise beyond FTNT's current accomplishments. Thus, while FTNT has the talent, the ambitious nature of this project carries a risk of not fully realizing its potential.
The Last Mile
The final leg of the data packet's journey, often called the application edge or the last mile, is where the connection is made with the target application, be it hosted in the cloud or on-site. FTNT excels in managing the on-premises application edge through a comprehensive suite aimed at boosting application performance and ensuring security. They offer products like FortiADC, which enhances application speed, reliability, load management, and security. FortiWeb, their web application firewall, includes API protection and is part of a broader array of security solutions covering DDoS and bot protection, alongside robust email security measures. FortiGate also plays a crucial role in this segment, handling the inspection of inbound traffic. While Fortinet's capabilities at the cloud application edge might not be as widely recognized, they remain formidable, with FortiWeb available in a SaaS model and VM-based cloud firewalls designed for straightforward deployment in cloud environments.
Wrapping Up
FTNT is very solid in the first and last mile. In the first mile (aka SASE), we would say FTNT’s PMF (Product Market Fit) is perfect but its GTM has been lacklustre to date. Though, this is likely to change as FTNT replays its SD-WAN playbook to its 700k installed base. The last mile is where FTNT is most mature and established, albeit less so in the cloud application edge. And the middle mile is where most long-term incremental value will arise, as once FTNT has a dense global PoP network driven mostly by its ASICs, it will be able to provide BoB NaaS, which is a promising trend still in the early days, and increase gross margins while remaining its competitiveness thanks to its vertical integration.
The middle mile segment is currently very fragmented and regionalized, except for a few global names. We expect FTNT to benefit from the value created by this segment being consolidated.
If, as we predict, FTNT can be a winner in the first, the middle, and the last mile, the company will be arguably the most pervasive networking and security name, and as we journey to this future point in time, sizeable shareholder value should be created.
Valuation Considerations
We prefer to look at the EV/(FCF-SBC) multiple and compare this with the Rule of 40 (inc. SBC) when doing relative valuation analysis. When applying this relative valuation FTNT looks attractive with a EV/(FCF-SBC) of 34x and a Rule of 40 (inc. SBC) of 37 (note, we calculate the Rule of 40 with NTM growth and LTM FCF margin and SBC %). Compare this to PANW with a Rule of 40 of 40 and an EV/(FCF-SBC) of 50x, and CRWD with a Rule of 40 of 42 and an EV/(FCF-SBC) of 215x, and you can see FTNT's attractiveness.
However, for companies with such a long-term durable growth outlook, it makes more sense to put more weight on a DCF valuation. Here is a snippet of our DCF valuation model for FTNT. The settings shown are for the base case: a 45% terminal FCF margin, a 10% CAGR for FY26-FY29 following the guidance/consensus forecasts for FY24 and FY25, and a terminal SBC % of 2.5%. Click the link to view the full model, showing the reconciliation from enterprise value to equity value and value per share. As can be seen, our base case suggests a ~50% upside for FTNT from the current price.
Conclusion
After years of being overlooked by Gartner, FTNT is now rapidly gaining acknowledgment for its unique approach to SASE and is starting to capitalize on the trend of preferring single-vendor SASE solutions. Our forthcoming Convequity Impulse review will cover this in more detail, but it already appears that FTNT is demonstrating increased prowess and living up to the expectations we've long held for it within the SASE sphere. However, SASE or SASO represents just one avenue for growth. The middle mile, where FTNT has the opportunity to offer NaaS, stands as another significant, yet currently underappreciated, growth driver by the market.
Beyond these growth opportunities, FTNT is also making strides in OT/IoT security, a segment of their business we've covered extensively, though we'll delve into that in a separate discussion. From a valuation standpoint, we believe FTNT is relatively undervalued, given its strong financial performance and business achievements, as reflected in the Rule of 40. Our baseline DCF analysis further supports this perspective.