Mini Security Series: Entry Barriers Part 2
Summary
This is a short report on the entry barriers of the 5 main areas of security we discussed in the April-22 PANW follow-up report.
In Part 3 we’ll discuss why NGFWs are still very important for orgs’ security postures.
After this report we plan on beginning the TSI research project where we’re going to navigate right through the tech stack, from sand to skies.
Intro
We thought assessing the entry barriers across the different areas of security would be interesting for investors because there are areas that seem quite easy to enter and others that are not. So, as an investor you may want to focus or refocus your cybersecurity allocation toward future winners of the higher entry barrier areas of security.
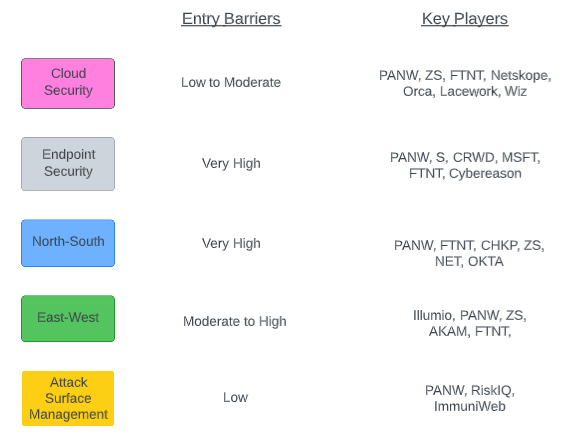
We used the following diagram in the April-22 PANW report, to distil the cybersecurity industry into 5 main areas. We’re going to reuse it as a framework for discussing the entry barriers for each area.
The following diagram is the TL;DR. Our view is that North-South and Endpoint Security are the areas with the highest entry barriers, followed by East-West, then Cloud Security, and then Attack Surface Management having the lowest barriers.
We shall elaborate on each area in the following text.
Cloud Security
In Part 1 we discussed that the cloud security market had low entry barriers because easily accessible IaaS from hyperscalers has made it so startups only need to innovate with some smart code – they don’t need to innovate deep into the software/hardware stack. Furthermore, opportunities arise for startups because big enterprises hate vendor lock-in and hence many CISOs are more than happy to back new BoB startups in new fields of security emerging.
For agentless solutions smart startups can easily enter the space because the onboarding is super frictionless as new customers would just need to allow the software to connect to their cloud network so it can scan for all the hosts. From there the agentless solution is deployed and ready to monitor things based on utilization on cloud provider APIs embedded in the hosts. There is also much less business risk with agentless solutions because there are no agents installed that could potentially block operations – all the monitoring is done out-of-band.
Agent-based solutions require more effort to deploy because they involve having an agent being installed on each host across the cloud infrastructure. IT teams are obviously aware of the added effort of such solutions and hence the vendor would most likely need to have an effective S&M operation in order to persuade IT teams that the investment in time and money will be worth it. Due to the longer sales cycle, agent-based startups will need to invest heavily in the front-end of the sales process.
PANW offers a mix of agentless and agent-based cloud security solutions. Detection can be adequately done with agentless but for remediation you do need an agent installed on the host that can block and eliminate malware and stop suspicious movements. One downside with agents is the drain on the hosts’ resources and as a consequence processing speed can be affected. Another downside is that they are more complicated to manage. A compromise many startups and more established security players are taking is lightweight agents accompanied by agentless out-of-band monitoring.
Orca Security is an interesting startup because they are going all in with the agentless approach – for CSPM, CWPP, and vulnerability management. However, their solution only looks like it can detect, alert, and do slick prioritization work – it doesn’t actually block live malware detected on a host directly. However, Orca has a back-end SOAR so theoretically they can get connected to inline tools (security tech that inspects data in motion like firewalls, SWG, and even endpoint agents) to indirectly execute threat blocking and elimination.
So, whilst Orca is a next-gen startup, we have mixed opinions about their BoB sustainability many years out into the future. Part of us thinks that because they are agentless-only, they should be able to be copied, but at the same time they are really next-gen in the way they’re doing this type of security.
So, having the agent-based solutions included in cloud security does somewhat raise the barriers to entry because not only does a wannabe copycat startup need to copy the code, they also need to spend a lot in S&M to overcome the deployment barriers in the minds of IT. But at the same time a comprehensive cloud security vendor also needs agentless solutions because there are many instances of non-IaaS components that can’t be supported by an agent. For example, orgs can't do serverless security via a host because they don’t have access to it. And for a typical IaaS EC2 deployment, you use Lambda, Gateway, EBS, S3, etc., and these auxiliary components don’t give IT teams direct access to the hosts. So, in these cases the out-of-band, agentless approach is the only way.
Surprise, surprise, because of the combo of agentless and agent-based solutions built into its Prisma Cloud platform, PANW will very likely continue to be a very strong BoB player in cloud security. But the others mentioned in the diagram above also have a bright future, in our opinion.
Endpoint Security
Historically we would say endpoint security has had moderate entry barriers because whether a vendor has gone the EPP route or the EDR route, there is either a heavy agent to be installed or a large labour-intensive cloud operation required, respectively. Now XDR has entered the scene, the entry barriers have risen higher because as we articulated in the recent S report, endpoint security has become a data engineering problem.
XDR requires the quick aggregation of data from a wide variety of sources into a data lake, and then queries into that data lake need to be super-fast and cost effectively to support security analysts in combating the bad actors trying to infiltrate. The legacy way of applying a generic SIEM and tuning it for security use cases was already proving highly inefficient for the EPP/EDR era, and so is certainly a poor way now we’re delving deeper into the XDR era.
The money spent by PANW on Demisto ($560m), CRWD on Humio ($400m), and S on Scalyr ($155m) are huge indications that the future of endpoint security will be driven by the back-end data lakes. In our recent SPLK report we highlighted how almost impossibly challenging it is for a legacy on-prem log management vendor to modernize with the cloud and turn a SIEM into something like a data lake. So, if SPLK isn’t going to be the answer, what else and where else can endpoint security players go to get better log/data management? They could build a new data lake from scratch though the risks are obvious because it would require very large investments to acquire the infrastructure and talent to build something like that.
Another option is to go with a data lake specialist like Databricks or even SNOW (because they’ve recently expanded from data warehouses to data lakes), but as their gross margins are c. 50% and 60%, respectively, in doing that an endpoint security vendor would be paying 50%/60% more compared to doing it themselves. And, of course, this would make them very uncompetitively priced versus PANW, S, and CRWD.
For these reasons we think PANW, S, and CRWD will extend their leadership in the XDR space, perhaps followed closely by FTNT (though FTNT hasn’t been recognized by Forrester in the XDR Wave). In their 4Q21 XDR Wave report, Forrester frequently mentions vendors’ cross-telemetry capabilities. They state that PANW is a leader in this and CRWD or S are not at that point yet. Most customer reviews in Forrester’s survey will be pre Humio and Scalyr acquisitions, however, so we expect the cross telemetry to have improved already.
North-South
Both on-prem and off-prem solutions require substantial hardware integration considerations and aptitude because it is the hardware that enables the real-time inspection of bits flowing through a network. It also requires supply chain management because the firewall/SWG vendor needs hardware to operate on.
Any potential new entrant threat to the top North-South players will likely come in the off-prem form, unless we see another change of the paradigm in the future. Though, for off-prem north-south security the same requirements of hardware knowhow and supply chain management apply. And inspecting packets is a resource-intensive undertaking and hence the computing costs are high, whether it is done in a colocation PoP or in a hyperscaler’s PoP. So, a new startup in this space would need a very large amount of capital if they were doing off-prem security.
The players emerging as SASE winners - PANW, FTNT, NET, ZS, and Netskope – are unlikely to get knocked off their pedestal because of these capital and supply chain requirements.
East-West
To protect orgs from east-west unauthorized movements segmentation has prevailed as an ideal solution. As discussed in the Ultimate Investor Guide to Zero Trust report, there are different types of segmentation.
There are network and hypervisor-based segmentation but there are limitations to doing it at these layers.
There are identity-based and host-based microsegmentations that both require agents on the endpoints/hosts. This is a software-defined type of segmentation that provides teams with full visibility of their network across various environments and allows them to enforce policy to prevent/allow certain types of connections across apps, machines, and services.
And there are NGFWs which are very capable at segmenting traffic flows but perhaps requires more experience to manage versus newer microsegmentation solutions.
The network-based segmentation entails hardware and hence for the previous reasons in the north-south section there are high entry barriers but this is a legacy way to segment so not that important >>> however, still very important for OT security because microsegmentation doesn’t work for these environments. The microsegmentation alternatives have lower entry barriers but not really low because of the agent requirements and the associated deployment effort. And a NGFW is a beast of a security tool – very much like a Swiss Army knife – and hence imitation here by new entrants is not likely.
To summarize, we would say investing wisely in players currently looking like future winners in this space – PANW, Illumio when it IPOs, ZS (although we’re not very fond of their solution), VMW, and definitely FTNT for OT security segmentation – would be smart because the entry barriers are moderate-to-high thus making it unlikely that newer startups will emerge and outcompete them or that established security players from elsewhere will successfully enter the fray.
Attack Surface Management
We presume entry barriers are quite low because whilst it’s clever technology, it basically requires scanning across networks and additional probing to ascertain the level of vulnerabilities of exposed devices. There are numerous startups in the space and PANW is the only major security player that has really committed itself, by buying Xpanse for $800m in Nov-2020. You may question why PANW paid $800m for a startup in a presumably small area of security, though Xpanse’s technology has been improved upon and incorporated into the Cortex line of products to boost its XDR and XSOAR. And recently Xpanse has powered the next evolution of AI-driven autonomous threat detecting, hunting, and remediation, named XSIAM, or Extended Security Intelligence & Automation Management.