Pre-IPO: Lacework
Summary
Lacework has an interesting backstory culminating in an All-Star leadership team and a staggering $1.3bn raised in November 2021. But right now, the company is going through tough times.
Nonetheless, the startup has a novel approach to cloud security and is worth learning about to further an understanding of the cloud security landscape and the future of cybersecurity.
We dive into Lacework’s machine learning security platform. We also explain the benefits and drawbacks of Lacework’s technology architecture, and also the cost disadvantage built in.
Lastly, we discuss Lacework’s advantages and disadvantages versus the competition, and highlight some risks to Lacework’s recovery.
Intro
Lacework is one of the key players in the race toward the goal of CNAPP (Cloud-Native Application Protection Platform). In November 2021, Lacework was valued at $8.3bn following its staggering raise of $1.3bn in its Series D, which is the largest funding round in cybersecurity history. Estimates available online indicate 2021 revenue was around $100m. If it wasn’t for the economic downturn, Lacework would probably be preparing for an IPO right now. Due to economic conditions and the impact on Lacework’s business, this isn’t the case, however. Though, for keen cybersecurity investors, we think its worth building some knowledge about this young company as they may eventually get back on their commercial track and the path toward an IPO.
Lacework is approaching cloud security by viewing it as a data problem. Much of the hype is centred around its unsupervised machine learning, which ingests large volumes of data to understand normal baseline behaviours, and then triggers high-fidelity alerts when a threat has been detected. With its ML technology, Lacework is addressing one of the biggest pain points in cybersecurity - the unmanageable volume of alerts. By reducing alerts by orders of magnitude and surfacing only the alerts that need urgent attention, Lacework allows SecOps to alleviate alert fatigue and to channel efforts toward more value-generating activities.
The ML platform combined with an agentless plus agent-based architecture, provides rich insights for prevention, compliance, detection, and speedy remediation. As Lacework continues to expand its scope of capabilities, it is one of the leading vendors in the race to becoming the first true CNAPP (Cloud-Native Application Protection Platform).
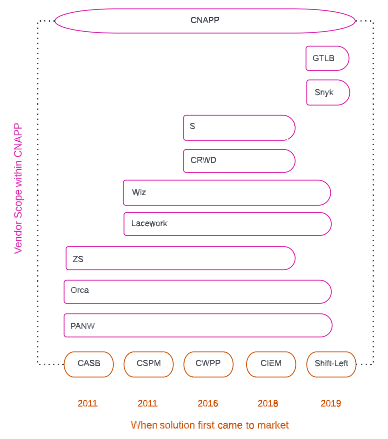
The Race Toward CNAPP
Source: Convequity
As we discuss in the Competition section, the agentless plus agent-based architecture gives Lacework comprehensiveness (and one of the winners toward CNAPP). It also scores them high in timeliness (i.e., the time difference between the presence of a threat and the detection of the threat). However, the agent component appears to be a significant cause of Lacework's troubles of late. At present, the industry is swaying more toward agentless approaches, which have speedy and lower-stress deployments. This is evident in Wiz's recent success. Lacework has recently attempted to address the issue by introducing an agentless workload scanning solution which is currently in beta mode. This should give its customers an easier way to scale out their environments in a secure manner. It's certainly an area of their business that deserves monitoring to see whether it helps the company turn around its outlook.
Backstory: CEO, Founder, Investor
Lacework has a CEO with substantial pedigree, the technical founder is very much still involved as the CTO, and it has the backing of a highly successful venture capitalist who is actively engaged.
Founder & CTO
Lacework was founded in 2014 by Vikram Kapoor. Prior to founding Lacework, Kapoor worked for nearly seven years at Oracle as a Development Manager for the company’s database products, and then 3+ years at Bromium as the Senior Director of Engineering. Bromium was an endpoint security startup that used micro virtualisation to sandbox (i.e., isolate) incoming traffic, like an email, a web page, or file, etc. to protect the device from potential malicious code.
Interestingly, Kapoor joined Bromium as the first employee only a few months after it was founded in 2010. He left the startup in its early stages, though his contributions helped Bromium raise its profile enough for it to eventually be acquired by HP in 2019. Following his departure at Bromium, Kapoor started Lacework as an Entrepreneur-in-Residence at Sutter Hill Ventures.
When considering Kapoor’s background, his motivation to create Lacework is clear. He has the skills and experience in databases and security, and wanted to combine these to bring a data-driven platform to the cloud security market.
Current CEO & CEO Backstory
The current CEO is Jay Parikh, who previously spent 11 years as the VP of Engineering at Facebook. Parikh is credited with building the data centre infrastructure that supports Meta’s numerous apps and services, and remarkably managed the engineering team expansion from 300 to over 30,000 engineers. The calibre of the current CEO is promising for Lacework; however, it’s worth pointing out that Lacework has experienced substantial CEO turnover for such a young startup – as we’ll briefly outline next.
In 2019, Dan Hubbard (considered a thought leader in cybersecurity and currently founder and CEO of Disrupt Security) became the CEO. And then in February 2021, Hubbard returned to his CPO role when David Hatfield was brought in as CEO (Hubbard left Lacework ten months later).
Hatfield has held executive positions at Akamai, Symantec, and Limelight Networks before serving as President at Pure Storage. Hatfield took charge of Pure Storage in 2013, when it had only 100 employees and little revenue. He then led Pure Storage to its IPO in 2015, and to becoming the fastest company in history to reach $1bn in annual revenue. Incidentally, Pure Storage was Sutter Hill Ventures' first major success, and provided the backbone for Mike Speiser's future investments, both in terms of capital and talent source.
In July 2021, Parikh joined Lacework (following two months in an advisory role), and both Hatfield and Parikh served as co-CEOs. Lacework has been hit hard by the economic downturn, having to lay off about 20% of its employees. Sidenote: this may imply that Lacework’s platform, being laid on top of Snowflake, which in turn is laid on top of AWS, leads to a product that is too pricey for customers, especially in the current climate. We’ll discuss this in detail later in the report. As part of a restructure to the business, earlier this month, it was announced that Hatfield is stepping down as co-CEO and will remain on the board, and that Parikh will be the sole CEO going forward.
The Leadership Team Going Forward
Indeed, there has been instability within Lacework’s leadership team. Notwithstanding the disruption, the startup still has an All-Star leadership team. Parikh as CEO and Kapoor as CTO, have recently welcomed distinguished security engineer Ulfar Erlingsson to serve as the Chief Architect. Erlingsson has a PhD in computer science from Cornell University, and among his long list of accomplishments, he serves as the Chair of the IEEE Technical Committee on Security and Privacy, has authored numerous publications, founded a startup acquired by Google that forms the basis of Google Chrome’s security, and worked at Google as a Manager for Infrastructure Security for several years.
Mike Speiser of Sutter Hill Ventures
Probably the biggest star of the All-Star team, however, is Mike Speiser. Speiser, Managing Director of Sutter Hill Ventures, is a VC with a differentiated approach that has proved to be highly successful. Rather than make a diversified set of bets across many startups, Speiser has a concentrated portfolio which has enabled him to focus more resources into his investments. It’s a risky strategy but has paid off handsomely.
In 2009, he became the founding investor of Pure Storage. And in 2012, he was the founding investor of Snowflake. In both these companies, Speiser served as the initial CEO and has been very involved in the huge successes of these tech pioneers. Quite incredibly, he turned his $200m stake in Snowflake into a $12bn valuation following Snowflake’s IPO in 2020.
Lacework is Speiser’s next major play. Again, he is the founding investor that provided the Entrepreneur-in-Residence for Kapoor back in 2014. And has been a key catalyst to the startup’s growth, connecting it with various customers within Sutter Hill Venture’s portfolios. It’s reasonable to surmise that the incredible Series D funding of $1.3bn, was largely driven by Speiser’s presence and other VCs wanting to piggy back on a known winner.
Product
Lacework’s platform is designed to help SecOps prevent attacks, detect attacks, and investigate attacks. And the company is expanding more into shift-left and shift-right areas of cloud security.
Prevention
It provides CSPM (Cloud Security Posture Management), which is a solution that operates agentless, using public cloud APIs to identify misconfigurations across cloud infrastructure, to remain compliant and to close loopholes before an attacker attempts to exploit them. It also provides vulnerability management by monitoring publicly available CVE (Common Vulnerabilities & Exposures) lists, and using these to scan customer cloud environments to identify potential weak spots.
More recently, the company has expanded into developer workflows, offering shift-left security solutions. In November 2021, Lacework acquired IaC (Infrastructure-as-Code) security startup, Soluble. This now gives Lacework the ability to automate IaC security and compliance for customers, enabling them to safely scale their infrastructure.
Detection
Lacework ingests vast amounts of data (collected via APIs and agents) from a variety of sources. According to management, it typically takes about two weeks for their unsupervised ML model to gain a good understanding of normal behaviour across the customer’s cloud environment. Once baseline behaviour has been established, Lacework will surface alerts when it detects anomalous behaviour. Alerts are stratified into different types across two categories – Anomaly and Policy – as shown below.
Source: Lacework, Convequity representation
Lacework’s unsupervised ML model obviates the need to manage unwieldy rule-based systems for detecting threats. With static rules-based systems a SecOps administrator must write and maintain lots of rules, each one created to detect a specific threat. This was manageable in simpler times when an enterprise’s entire infrastructure may have been in a single server room on-prem. The problem, however, is shifting to the cloud has resulted in an exponential increase in things that need attention, while rule-based systems can only expand linearly. Thus, there is an inherent lack of coverage when using a static rules-based system. Even if it can provide adequate coverage against threats, it needs a number of admins to continually add/remove rules which, of course, is costly and time consuming.
Most admins attempt to manage such systems by adding more and more rules as new threats emerge. Though, this invariably results in excessive restrictions. For example, when a DevOps engineer needs to set up something for a new microservice, it will most likely be flagged as suspicious. At the same time, the rule that was forgotten or missed will most likely be the one that lets a threat slip through the defenses. In short, the management of rules-based detection is like trying to predict the future in a very complex environment.
Lacework has targeted this pain point with its ML platform that requires zero rules or tuning. The solution is deployed in default mode, and allowed to ingest and analyse data until it has an accurate understanding of baseline behaviours across the aforementioned alert types. The end result is that:
SecOps have more time to spend on greater value-adding activities.
Detections are predicated on contextual information, whereas static rules are more singularly focused.
The detections evolve with the environment and threat landscape.
Investigation
Lacework has a pretty good platform for facilitating shift-right activities. Their Polygraph technology is a visualization tool that supports SecOps/SOC to triage, investigate, and remediate threats that have been alerted to them. As Lacework sits on top of Snowflake infrastructure, Polygraph also gives SecOps the ability to quickly query and retrieve data – going back 90 days as the standard data retention package, and 180 days if additional storage is paid for. So, in using Lacework, enterprises don’t need to make costly transfers of data to a SIEM. SecOps is further supported by Lacework’s various third-party integrations, which enables Lacework to ingest other sources of data to enrich its ML model.
Here is a snippet of the Polygraph in action. It provides of visualisation of how accounts, instances, services, users, etc. are connected. When an alert is triggered, the Polygraph will stitch together the prior events that led to the alert, laying out the who, what, where, when, and why. For example, the ML model might have noticed an unusual occurrence whereby someone created a new AWS account in a particular region for the first time. They then connected that account to a S3 bucket to extract some data, and then deleted the account. The Polygraph will map out this series of events so that SecOps can quickly determine that the alert indicates a breach. The DIY alternative is for SecOps to collate the logs from AWS’ CloudTrail, but as these events occurred in different AWS services, it would require much time and effort to understand how each event is connected.
Source: Lacework
The following diagram, taken from Lacework’s website, summarises how Lacework helps protect enterprises in the context of a cyber attack – via the aforementioned prevention, detection, and investigation.
Source: Lacework
Architecture
As mentioned earlier, Lacework has been built on top of Snowflake. Kapoor becoming Entrepreneur-in-Residence at Sutter Hill Ventures with Mike Speiser as his mentor, meant that Snowflake, as the data warehouse, was an obvious choice.
Though, the great fit between the two companies is not purely based on business relationships – technically, Snowflake is also a great fit for Lacework. Kapoor wanted to improve upon existing cloud security solutions by developing a multi-cloud, data-driven product that improved the efficacy of alerts and facilitated speedier investigations. And Snowflake is the ideal partner for this because its data warehouse can be laid atop AWS, Azure, and GCP (and even on-prem), and the novel separation of compute and storage enables unrestrained data processing and unrestrained data retention.
Thanks to developing its solution across Snowflake, Lacework is now processing c. 60 PB of customer data per day. So, unlike the case when using SIEMs, customers using Lacework no longer need to choose what data to save, and for how long. And they can frequently scan their environment and query their data without excessive waiting times and incurring excessive costs.
Equally important, Lacework aims to assist SecOps in understanding the full context surrounding events, not just single points of data. To achieve this requires scale and the efficient organisation of data. With Snowflake’s unlimited compute and storage, Lacework has the capacity to deliver this level of context for customers.
Aside from the modern data stack, the other notable observation regarding Lacework’s architecture is that it consists of agentless and agent-based solutions. Next-gen vendors like Orca and Wiz, have opted to approach cloud security with purely agentless solutions. Endpoint security vendors like CrowdStrike and SentinelOne, have entered cloud security with a bigger focus on agent-based detections. Lacework isn’t entirely unique here, because Palo Alto Networks also has agentless and agent-based detection methods. However, it could be argued that Palo Alto Networks has somewhat haphazardly evolved into this dual agent/agentless architecture, whereas Lacework has designed it this way since inception, and more significantly, on a cleaner slate (and hence less technical debt and complications).
One observation is that, until recently, Lacework's agentless and agent-based suite of solutions were sold as one SKU (Stock Keeping Unit). In other words, its agentless solution (CSPM) wasn't sold as a standalone product, it was sold together with the agent solution (CWPP).
As the industry has been favouring agentless approaches, not having an independent agentless SKU has hurt Lacework. Wiz, on the other hand, which is a purely agentless vendor, during the pandemic became the fastest ever cybersecurity firm to reach $100m of revenue. In a somewhat late response, Lacework has recently introduced an agentless workload scanning solution that can be bought as an independent SKU.
It seems as though enterprises are prioritising scalability at present, which is why agentless vendors are in high demand. The new agentless workload scanning solution is still in beta mode, but could be significant in helping Lacework turn things around, by giving customers an easier way to scale their environments securely.
A Deeper Dive into Lacework’s Product
There are three primary methods in which Lacework collects data for its customers – cloud logs, container repositories, and runtime environments.