Perspectives - S - The Next NGAV (2/3)
This is the second article of a three-part series on SentinelOne (Ticker: NYSE:S). Here we share insights on the firm's GTM strategy and its financial metrics.
Welcome to Covequity's Quick Takes1— Timely interpretation of news & special events for cybersecurity and enterprise tech investors. If you are new, you can join our email list here:
Sources of Alpha: Complexity of the Business
Expected Price Appreciation: 500% from $45 within 5 years2
Executive Summary
SentinelOne is one of the most, if not the best, private cybersecurity companies going public in 2021. Its technology and vision are highly promising. (Article 1/3)
The company is executing an audacious GTM strategy following its years of stealth R&D. This means deep negative margins and operating metrics on paper. (Article 2/3)
Although skepticism may rise alongside a possible correction upon S’s lockup expiry, over the long haul, we view S as one of the best cybersecurity companies for its tech advancement. (Article 3/3)
Comparing CRWD & S
On the whole, we view S’s GTM as highly promising for its well-targeted product bundles in comparison to CRWD and broader legacy AV vendors in general.
For simplicity, we are going to cover CRWD mostly for its close competition with S3.
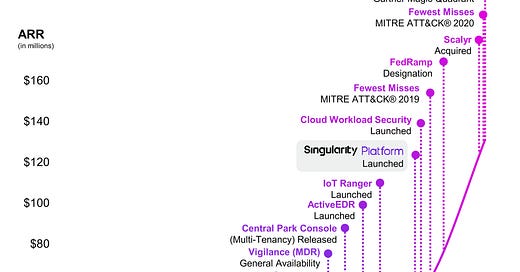
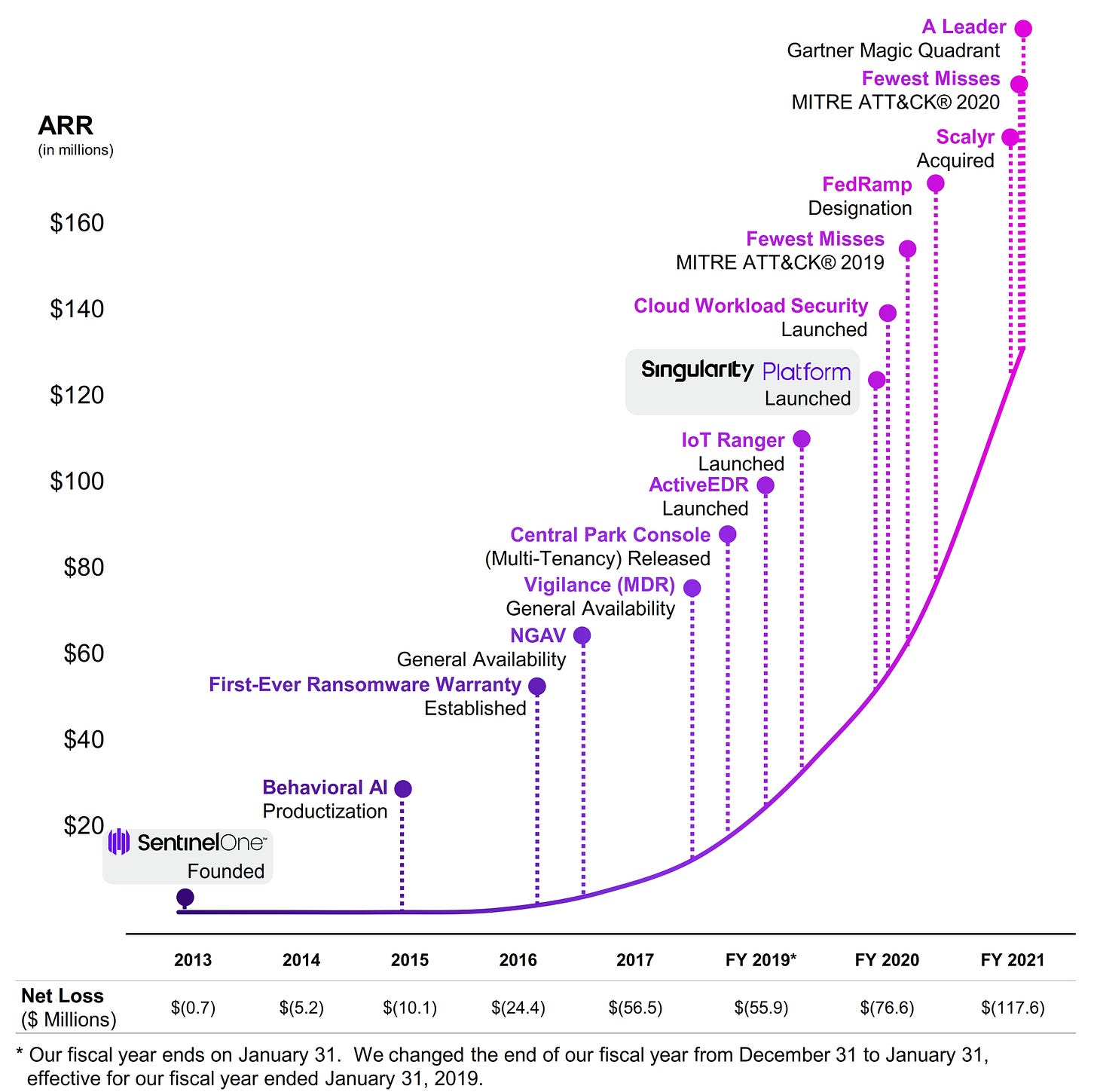
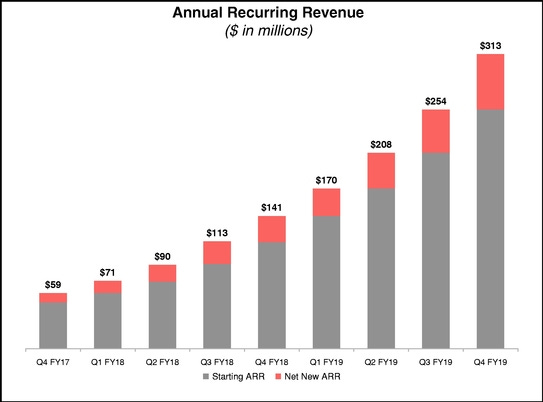
ARR & Milestones
In many ways, S is CRWD’s NGAV/EDR twin that chose the tougher-yet-potentially-more-rewarding route. CRWD was founded in Nov-11 while S was founded 14 months later, in Jan-13. However, there is a large difference between the two’s ARR: in Jan-20, CRWD’s was $1.05bn while S’s ARR at the latest quarterly figures is $161mn (Apr-21). This isn’t related to weakness in products or business, but a difference in strategy.
CRWD chose to build the product fast, test it and deploy it to clients very early on with huge expenditure in marketing while new products are being developed.
In contrast, S primarily focused on comprehensive R&D for many years and did not spend tons of money on marketing, making grand claims on product efficacy, until the product matured enough for massive adoption.
In our opinion, S’s founder and CEO, Tomer Weingarten, has a paranoid pursuit for technical superiority instead of making money early on. This is typical of a visionary company. However, what’s more favourable to investors is that Tomer isn’t trapped into the tech leadership only - he is also very aware of the hard lesson that good tech means nothing without good marketing. This is something missed by quite a few great startups and technically visionary companies.
Weingarten is an ambitious and skilled engineer, though what’s more exciting for us is that he isn’t trapped in R&D. He understands the typical mistakes made by engineers - that great products don’t matter without great S&M.
We spent years in R&D and didn’t push the S&M pedal until we felt comfortable with the completeness of the product in c. 2017….
…as an engineer, one of my takes in running S is that marketing is as important as the technology itself.
-S CEO
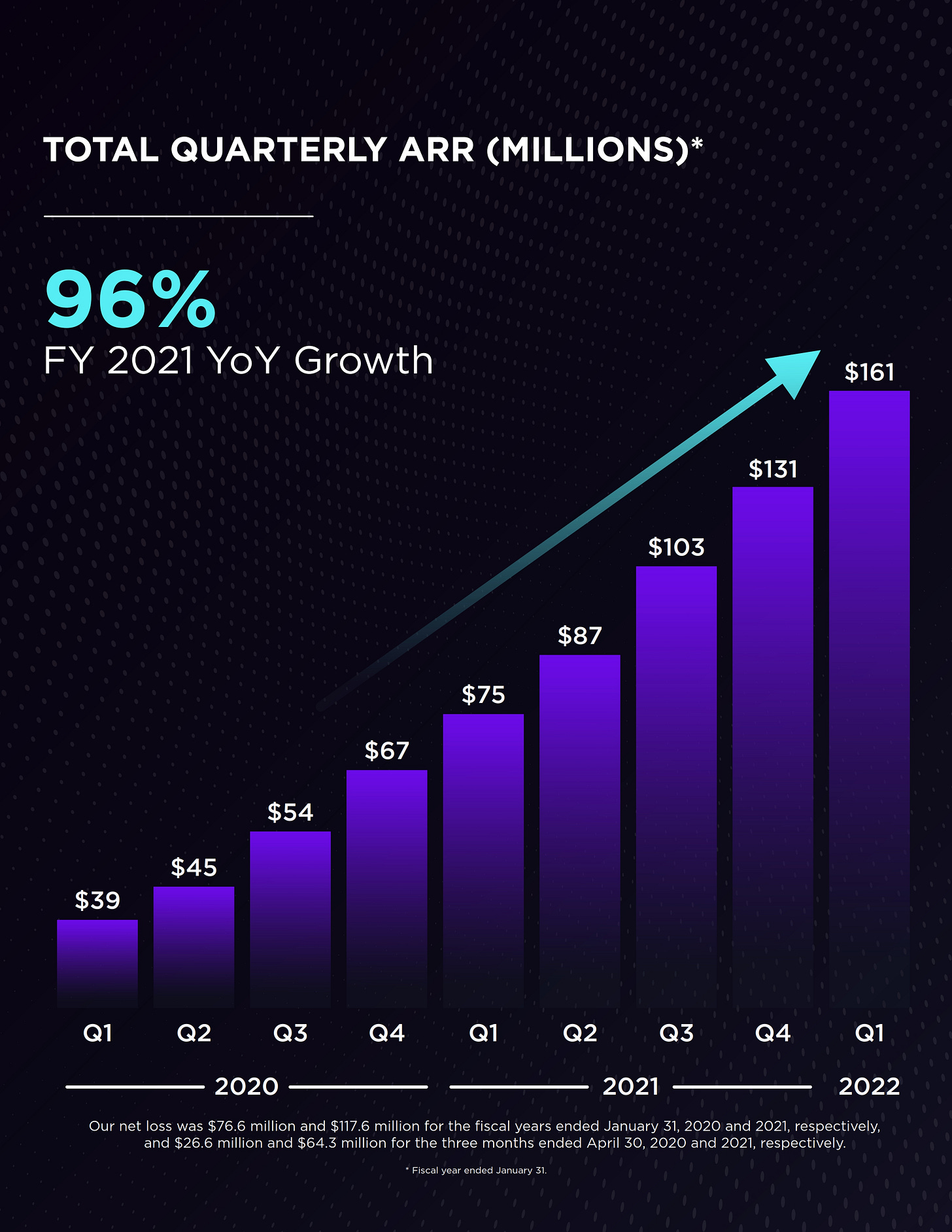
As you maybe find in S’s milestones graph, most of the core functions were developed before 2017 and most of the peripheral ones - Vigilance (MDR), Central Park Console (SOC), ActiveEDR (Automation), and IoT Ranger (IoT Security) - were finished around 2019. With the completion of a solid suite of products, S’s Singularity Platform was released and its GTM engine began to run at full speed, scaling the ARR from $39m in 1Q20 to $161m in 1Q22.
The numbers track CRWD’s ARR scaling very closely:
The major difference between CRWD and S is the former started the monetization very early on with EDR being the core product and the backbone of the Falcon platform. Subsequently, more modules leveraging the sensor residing in the endpoint and the log data in the cloud were introduced as part of CRWD’s growth strategy.
DBNR & Sales Channel
CRWD’s sales strategy is the typical land-and-expand playbook. An enterprise customer selects a small group of user endpoints to try out CRWD’s products, most of which started with EDR and super easy configuration.
The setup is highly supportive for the SaaS businesses’ land-and-expand strategy and CRWD has benefited from this tremendously as the DBNR has consistently been above 120% post IPO. This is in large part driven by CRWD’s channel strategy; instead of going through a two-tiered sales distribution channel (from CRWD to wholesaler to reseller), CRWD leverages resellers directly to land customers and then builds relationships later with additional module sales. This also means that CRWD needs to milk more from its customers - 4Q19 147% DBNR is a good example of how to make the numbers higher before IPO:

This strategy doesn’t come without any stress. S, on the contrary, decided to sell the entire platform as a bundle, instead of à la carte style like CRWD. By bundling everything together that a sophisticated enterprise client might need, S’s Singularity platform product has a lower total cost compared to ticking every module from CRWD and pay a huge premium. Furthermore, S is deliberately running 100% with the two-tier distribution channel, which means that CRWD’s top end of the funnel is limited as channel partners want to befriend S rather than sending business to CRWD.
As opposed to our closest competitor CRWD, we chose to go 100% with the channel and we’ve built a great relationship with them.
-S CEO
Coming Head to Head
The competition between S and CRWD is ferocious, possibly squeezing other weaker hands out of the main battlefield.
We met, competed, and won over Crowdstrike for 70% of the time when approaching the clients.
-S CEO
One would expect S to grab market share and generate early parabolic growth mostly from legacy AV with super easy GTM. On contrary, however, S has spent 70% of the time competing with CRWD while posting 96% growth and showing the similar momentum to CRWD who generated growth over the decline of legacy AV vendors.
Fundamental Drivers to S’s Edge
We believe there are a few fundamental drivers to S’s strong competitiveness against CRWD.
Better product effectiveness
Better user experience
Better price (bundle)
Looking across the tests, it is pretty clear to us that CRWD’s effectiveness in protecting the endpoint has been grossly exaggerated. We come to this conclusive judgment based on a few facts:
AV-Comparatives & NSS Labs
Across a few AV tests carried out by names like AV-Comparatives and NSS Labs, CRWD isn’t able to demonstrate superiority in terms of detection rate relative to legacy ones. That is more so given the context that CRWD doesn’t allow easy out-of-the-box test. CRWD requires pre-acknowledgment to do the test in order to prep the software. This is also the main reason behind CRWD’s lawsuit against NSS Labs, a not-for-profit cybersecurity testing agency, back in 2018. CRWD claimed that NSS Labs did the test with software acquired from another reseller, and the test result - a 60%+ detection rate, the lowest across the board - was released without CRWD’s agreement. NSS Labs eventually went insolvent and dissolved the operation in 2020.
MITRE ATT&CK Test
However, when it comes to the MITRE ATT&CK test4, not so lucky this time. In the first two rounds of the test (APT3 2018 and APT29 2019), CRWD delivered legacy-AV-like results. If the name was disguised, we have no doubt that no one could identify CRWD out of the group. In the latest round of the test (Carbanak + FIN7 20205), we see lots of legacy AV vendors improved the overall detection rate via gaming the test, and surprisingly CRWD seems to follow their modus operandi as well.
CRWD’s marketing on Reddit to technical guys backfired
CRWD quickly prided itself as the winner in one Reddit post6. This soon went sour as skeptics (and this is in the official CrowdStrike subreddit) quickly compounded around CRWD’s lacklustre results, over-marketing, and the hypocritical narrative built up by the CRWD team. The following quote from one comment is very telling.
·4m·edited 4m
I have to say... almost none of those graphs seem to marry up with the report...
Or too focused on detection count rather than triggering a response (meaning manual work required) which has little value if it doesn’t trigger a response... people don’t want incident response... they want a trigger and block
Out of the 15 attacks, 3 went through - 2 with no notable information
174/231 - detection count
64/174 - analytics coverage (37% successful)
141/174 - telemetry (81% successful)
152/174 - visibility (87% successful)
Almost seems to purposefully hide data because multiple vendors did better in everything reported but they aren’t shown, only those who did worse (example, leaving SentinelOne off charts to make cs look good)
Almost boarders on false advertisement
….
·4m
Sorry, was meaning the fact s1 is missing from their graphs shows the data is wrong because it should show cs as not doing well, but they left it out and compared only to those who did worse
Edited it to hopefully make more sense
CRWD’s reaction to this post is also very insincere. The post is blocked for further comment and the team admitted shortfalls saying others are acting the same and did not address the thorny issues directly. Interestingly, S has been missing across many CRWD marketing materials in their effort to solidifying CRWD’s unchallenged position in the NGAV space. More importantly, from S’s interpretation of the test result, we found the missing piece of the puzzle explaining why legacy vendors like Trend Micro along with CRWD improved the results dramatically this time - tweaking the configurations.
CRWD’s human intervened config changes
With tons of manual configuration changes specifically optimized for each step, there is no doubt that tools that are full log aggregated are able to deliver a high detection rate. However, that also means less effective protection for real users. The lesser-than-marketed effectiveness, especially compared to newer NGAV vendors, combined with weaker user experience in terms of automation, puts CRWD’s future in a dubious spot. Instead of a BoB solution winning the long term, CRWD may need more S&M tricks to solidify its status and growth.
CRWD’s first poor prevention test result
In the latest round of the test, the protection test is added as well and vendors can choose whether to publish it or not. CRWD missed 3 out of 10 tests while S missed 1, according to S’s narrative the backend did stop the threat in the end but came in three minutes later.
CRWD’s complex configuration & SKUs
MITRE also offers detailed configuration on participants. As you can see from the following charts, CRWD slide is complex and messy with two agents and seven individual modules/SKU). This is due to its platform modules upselling strategy that divides point functions into independent subscriptions. The configuration is more finely tuned than S, typical of a more legacy vendor who tries to patch over things.

CRWD Product Versions and Configuration for Carbanak+FIN7 test Source: MITRE 
S Product Versions and Configuration for Carbanak+FIN7 test Source: MITRE
CRWD’s founder parallel with ZS?
The co-founder and CEO, Kurtz is a charismatic person who does not shy away from overpromising marketing, and direct attacks at competitors, and even not-for-profit testing agencies - notable parallels with ZS’s Chaudhry.
S’s last mover advantage
In comparison to CRWD specifically, S has a better detection rate, provides richer context, better automation, and better user experience.
We believe the better detection comes from a combined effort of leveraging static AI on the endpoint and better algos powered by better context enrichment backend. This backend allows S to have a better understanding of what’s going on with the endpoints and the network.
The granular contextual information combined with advanced ML/AI algos in classifying activities between the suspicious and malicious makes ActiveEDR emerge as the natural evolution of the first-gen pure EDR. EDR marked a major breakthrough in endpoint protection as all the key log data is archived and aggregated to the cloud for human experts to leverage and deliver better malware detection and response. However, pure EDR is more labour intensive and less automated. S takes it a step further with ActiveEDR which delivers a preliminary automated response as long as the threshold value between suspicious and malicious is met. And this further alleviates the workload for SOC analysts.
This is further empowered by S’s well-thought SOC automation solution that integrates the SOC function with EPP and EDR natively. CRWD instead used a clumsy and legacy host-based SPLK solution for log analysis and query. The two companies also came across each other in the acquisition of Humio and Scalyr, both of which are startups in log analysis focusing on reducing the cost of data hosting and analytics. Both Humio and Scalyr have the promising tech to solve the issue around the cost associated with storing large amounts of log data for long periods. However, Humio is more mature with a 600M+ price tag attached, we believe this is due to CRWD’s urgent demand to improve its internal data analytics capability and move away from the expensive and inefficient SPLK technology as quickly as possible.
Comparing the product descriptions
From the configuration page, we are also able to take a quick glimpse into CRWD and S’s product description:
(CRWD) Product Description
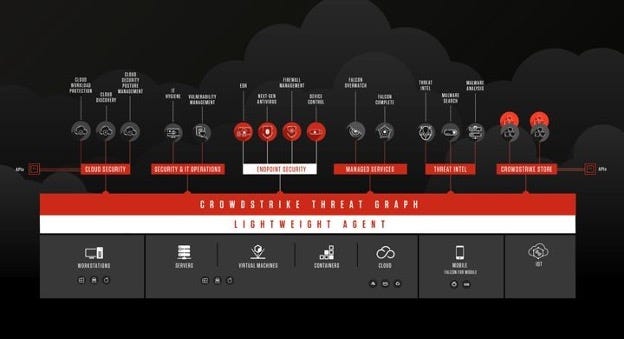
CrowdStrike® provides cloud-delivered endpoint and workload protection. Leveraging artificial intelligence (AI), the CrowdStrike Falcon® platform protects customers against cyberattacks on endpoints and workloads on or off the network by offering visibility and protection across the enterprise.
CrowdStrike Falcon delivers cloud-native endpoint security for a wide variety of platforms and workloads. It provides advanced detection and prevention functionality through its next-gen AV (Falcon Prevent), EDR (Falcon Insight) and Falcon Device Control modules, proactive human threat hunting (Falcon OverWatch), IT hygiene (Falcon Discover), vulnerability management (Falcon Spotlight), management of local OS firewall (Falcon Firewall Management) and integrated threat intelligence (Falcon X).
Falcon’s cloud-native architecture significantly reduces deployment time and management costs, and also benefits from crowdsourcing of threat information from millions of machines it protects in more than 170 countries and the analysis of trillions of security-related events per week originating from these systems. All capabilities are delivered through a single lightweight agent, reducing resource utilization and overhead.
CrowdStrike Falcon's cloud-native architecture leverages both smart sensor technology and CrowdStrike’s proprietary Threat Graph, a purpose-built distributed graph database in the cloud, to enable rapid detection, prevention, and response to all types of threats. CrowdStrike Falcon uses behavioral Indicators of Attack (IOA) and machine learning technologies to detect and prevent malicious behavior at various stages of the attack lifecycle.
The OverWatch managed threat hunting service consists of a global team of elite threat hunters whose job it is to be both the last line of defense to find a previously undetected intrusion, as well as to help customers understand and prioritize the threat information provided by Falcon and help them to stop a breach. OverWatch feeds discovered intelligence back into the product in the form of IOAs that describe newly discovered attack techniques, ensuring that any future occurrences of the newly discovered tradecraft will be automatically and immediately detected. This human-computer interaction forms a virtuous cycle that continuously improves the product to stay ahead of the adversary. OverWatch was not specifically scored during this evaluation, and their activity is not reflected in the reported results.
The CrowdStrike Falcon management interface has adopted the MITRE ATT&CK framework to provide a uniform and widely adopted language for describing suspicious and malicious behaviors it has detected or prevented.
(S) Product Description
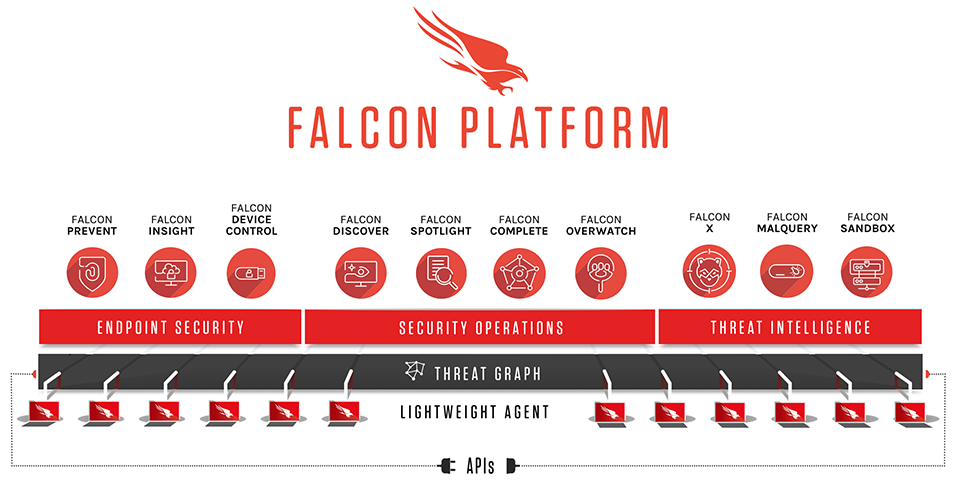
The SentinelOne Singularity™ Platform consolidates endpoint protection (EPP) and enterprise detection and response (EDR) into a single agent for Windows, Mac, Linux, and Kubernetes and supports end-user, server, and cloud-native workloads. Management is principally a cloud-delivered SaaS with global hosting region choice, but we also support hybrid-cloud and on-premise implementations. SentinelOne replaces or complements AV, adds EDR capability, and enables network visibility. Our EPP+EDR consolidation is highly uniform across OSes in order to create security operational consistency across compute types with an overall goal of lowering mean time to respond (MTTR) through automation.
Agents have several roles in the architecture including autonomously and automatically creating attribution context and cross-process event correlation in real time. This machine-built context, also known as Storyline™, is used for EPP purposes to identify and respond to malicious “stories” (attacks) at the moment they are detected. For EDR purposes, Storyline context is preserved on our platform for up to 365 days for fully customizable automated and ad hoc threat hunting across long time horizons and incident response operations. Agents will trigger appropriate responses within the device automatically or as commanded by the SOC. Via policy, customers can take advantage of either EPP or EDR modes or combine them into a consolidated EPP+EDR mode.
Storyline attribution mechanisms provide data enrichment beyond simple process tree tracking; SentinelOne differentiates by our ability to identify and handle key infiltration and attack techniques as defined by the MITRE ATT&CK® framework. In the case of Windows, the endpoint agent monitors, via kernel driver, user mode processes and their deep relationships including execution of APC to a remote process, RPC requests from a system process, and more, all of which are "re-attributed" to the original caller even across system reboots. Though Linux/Kubernetes agents operate in user space and Mac agents adhere to Apple’s “kextless” requirements (neither tainting the kernel), agents for these OSes accomplish much of the same “prevent-detect-respond” objectives as our Windows version. Our design enables Singularity agents to protect endpoints from malicious activity at any stage in an attack chain–from the successful exploit to the last payload operation. They detect threats both pre-execution using a machine-learning based file scanner and on-execution using unique behavioral AI engines. The EDR engine facilitates threat hunting and response investigation by collecting multiple OS events (process, file, network, user, DNS, registry, and more) with full context attribution. All of this machine-built metadata context is live streamed (or queued if offline) to the Singularity platform where it is evaluated in real time against customer-defined queries and SentinelOne-defined intelligence hunt packs. Agents offer various automated response actions to control emergent threats and recover systems back to a pre-infection state all without tedious custom scripting.
Note the difference in CRWD & S’s description. S’s description is well-targeted for making a step ahead of CRWD’s.
CRWD stresses its:
use of multiple modules;
Threat Graph in the cloud;
Falcon OverWatch Managed Detection & Response product with “human-computer interaction forms a virtuous cycle that continuously improves the product to stay ahead of the adversary.”
S on the other hand addresses the lateral issue around CRWD’s innovations
EPP and EDR are consolidated as a single agent and work more organically (CRWD relies more on EDR).
Management could be deployed on-prem or hybrid (CRWD offers cloud only);
EPP+EDR consolidation is uniform across all OSes (CRWD’s Linux and Mac support are notoriously bad).
Agents can do context enrichment, AI/ML correlation, and automatic response, locally in real-time. (CRWD’s agent is super lightweight sensor, these functions require help from the cloud).
Storyline could save up to 365 days (CRWD only saves up to 90 days). S’s GM is close to CRWD’s GM before shifting from public cloud to colocation - S must have better log storage & analytics capability in-house.
Agents could trigger response locally or guided by SOC in the cloud.
“Agents offer various automated response actions to control emergent threats and recover systems back to a pre-infection state all without tedious custom scripting.” (CRWD takes a more labour intensive approach to these functions)
S comes with lower prices
Talking about the price, this is the part where our conviction on the likelihood of S’s GTM success grows. CRWD is actively selling at a premium strategy - much like OKTA and PANW, and this is great for a BoB SaaS company as the premium pricing combined with premium products works great for long-term growth. However, given S’s higher efficacy and more advanced architecture, CRWD’s leadership is in a serious challenge. What’s more concerning to CRWD is that S decided to bundle everything together as Singularity Complete instead of dividing each piece of function into modules for sales on the platform marketplace.
The tiers of our Singularity Platform include:
Singularity Core. Our entry level security solution for organizations that want to replace antivirus tools with our EPP which we believe is more effective and easier to manage than legacy antivirus and next-gen antivirus products. Singularity Core includes our Static and Behavioral AI models and autonomous threat response and rollback features.
Singularity Control. Made for organizations seeking best-of-breed security with the addition of our “security suite” features for endpoint management. It provides additional features for control network connectivity, USB and Bluetooth peripherals, and to uncover rogue devices.
Singularity Complete. Our flagship offering that includes our full suite of product capabilities.
S S-1 filing
Price quoting - CRWD starts to fear S?
CRWD’s quote is generally 2x-3x of S’s comparable bundle.
Usually, you need to buy NGAV which is the Falcon Prevent module and EDR which is Falcon Insight.
However, CRWD decided to enhance its DBNR, and hence the device control is separated as another independent module.
These three bundled together are necessary for most clients.
The combined pricing is well beyond the price quote from legacy AVs, which is perfectly fine if the product quality is way ahead of the others.
Clients who mentioned “SentinelOne” in the discussion with CRWD salespeople would immediately have the pricing down by 50%+.
However, the resultant bundle price is still ~30%+ more than S, and moreover, CRWD loses the competitiveness on things like storing logs for up to 365 days.
Is S’s pricing sustainable over the longer term?
S’s pricing doesn’t come without drawbacks - it has priced its better product at a lower price and with more benefits, for instance saving logs for 365 instead of 90 days is a huge cost. The GM has dropped from 63% straight to 51%. However, we don’t think that is a viability issue as the cost is associated with the IaaS hosting cost and should S gain enough scale to go with proprietary colocation data centers, it could follow CRWD’s GM expansion from 54%+ to close to 74%. With Scalyr’s novel approach to reduce the overhead associated with log storing and analytics, we believe S’s end state GM could go to 80%.
On S&M and R&D, we believe spending as much as you can before the enemy got the time to fight back is the right strategy and given S’s strong product edge and PMF, 100% S&M to revenue is reasonable as long as S can continue to deliver the growth. DBNR has stayed around 120% level and the 100K+ customers continue to grow quickly. The gross retention rate comes in around 97%, typical of a solid enterprise company.
Overall, considering S’s positioning and S&M strategy, we think the numbers are lining up nicely and S has great room to improve its margin in the future with clear visibility.
That's one area where I think Sentinel One has done a nice job, they're logging every single process, file access, DNS lookup, network activity, etc., and they've made it really easy to search. The data is very similar to EDRs like Carbon Black. Bitdefender EDR captures the same data, but it's almost impossible to search, and the alerts are very difficult to research.
But, to your point, most small MSPs aren't going to invest in a SOC and won't know what to do with that EDR data, so I'm not sure a nice UI is that important for data that will never be touched.
the management console. This is one area where we totally get the SentinelOne love. They've created a user experience that puts every other endpoint vendor to shame. 7
We pioneered the world’s first purpose-built AI-powered extended detection and response, or XDR, platform to make cybersecurity defense truly autonomous, from the endpoint and beyond. Our Singularity Platform instantly defends against cyberattacks - performing at a faster speed, greater scale, and higher accuracy than possible from any single human or even a crowd… Our XDR platform ingests, correlates, and queries petabytes of structured and unstructured data from a myriad of ever-expanding disparate external and internal sources in real-time. We build rich context and deliver greater visibility by constructing a dynamic representation of data across an organization. As a result, our AI models are highly accurate, actionable, and autonomous. Our distributed AI models run both locally on every endpoint and every cloud workload, as well as on our cloud platform. On each endpoint and cloud workload, we run highly optimized AI models in a single lightweight software agent. Our Static AI model predicts file-based attacks of all types, even previously unknown threats, often referred to as “zero-day attacks,” with extreme precision in milliseconds. Our Behavioral AI model maps, monitors, and links all behaviors on the endpoint to create rich, contextual narratives that we call Storylines. These high-fidelity Storylines are continuously evaluated by our Behavioral AI model. When activity is deemed a threat, our software autonomously takes action to kill the attack. Because Storylines contain a complete record of unauthorized changes made during an attack, we are ready to remediate or roll back these changes. The power to turn back time on a device is unique in the market. It is the ultimate safety net and exemplifies autonomous cybersecurity. Thus, our software eliminates manual, expensive, and time-consuming incident cleanup.
CRWD sells USB/Bluetooth device controls individually, while S bundles it in the SentinelOne Complete bundle. This raises quoted prices by c. 20% for CRWD versus S while it is a huge native drawback for CRWD’s technology. CRWD’s lightweight agent puts heavy weight on the cloud. This means that when the device is roaming offline, the attacker has a higher success rate. Making things even worse, very often USB sticks could be the source of malicious files when CRWD’s cloud is out of touch with the endpoint8. However, CRWD has a solution but doesn’t sell it for free, but as an optional module costing customers 10%-20% more. We believe this is typical of the sales strategy imposed by CRWD and it explains why its DBNR has been so high consistently - it is selling functions that are crucial for customers as a way to milk more revenue growth.
Related Materials:
SentinelOne -Bringing Endpoint Detection Response into the Modern Age [Webinar]
Anything discussed in this post should not be treated as investment advice. For further disclaimer and disclosure, always refer to Terms Of Use for Convequity Ltd.'s Research
Assuming no further dilution, within five years, S will be grown into $50bn in market capitalization.
PANW’s Cortex XDR is also a very strong competitor based on our observation of its performance and integrations with PANW’s broader platform. However, it seems like the product is very new and had only gained little traction last year with a huge revamp in the product. We are also aware of newer vendors like Cycraft and Intercept X who also managed to create something new but haven’t kicked off the massive GTM yet.
For context, the test is done by MITRE Engenuity, a federally funded research and development centre for cybersecurity and backed by Cybersecurity and Infrastructure Security Agency and the FBI. The test is highly transparent, advanced and transparent, for a quick look, check the visualized version from Elastic here.
https://mitre-evals.kb.europe-west1.gcp.cloud.es.io:9243/login?next=%2Fapp%2Fdashboards%3Fauth_provider_hint%3Danonymous1&auth_provider_hint=anonymous1#/view/c2184e40-a13a-11eb-9d57-5de8e1bfb5ea?_g=(filters:!(),refreshInterval:(pause:!t,value:0),time:(from:now-15m,to:now))&_a=(description:'',filters:!(),fullScreenMode:!f,options:(hidePanelTitles:!f,useMargins:!t),query:(language:kuery,query:''),tags:!(),timeRestore:!f,title:'Round%203',viewMode:view)
https://www.reddit.com/r/crowdstrike/comments/mvt4rj/crowdstrike_achieves_100_detection_coverage_in/
https://www.reddit.com/r/msp/comments/gb47hq/nextgen_av_vs_established_players_i_dont_get_it/
Lies and Damn Lies: Getting Past the Hype of Endpoint Security Solutions